Because the internet is being broken by governments, internet service providers (ISPs), and corporations.
Broken by governments
Around the world, governments are using the internet for social control, through both surveillance and censorship. Many countries, such as China, Iran, and the United States practice active surveillance of the social relationships of everyone and the European Union countries require all ISPs and website operators to record and retain personal data on your behavior. With three-strikes laws, many countries now deny citizens access to the internet if accused of file sharing. Some countries even forbid the use of communication technologies, like Skype and Zoom.
Broken by ISPs
Internet service providers are breaking the internet too. They happily cooperate with government repression, they practice intrusive monitoring of your traffic through deep packet inspection, they track your DNS usage, and they get people thrown in jail, expelled from school, or banned from the internet, merely from the accusation of copyright infringement. Also, ISPs typically limit you to one internet address. If you want to share your internet connection with multiple devices, you must put all the devices on a local network. This works OK if you just want to browse the web, but makes life difficult if you want to take advantage of many applications.
Broken by corporations
Corporations have discovered how to make money from the internet: surveillance. By tracking your online habits, advertising companies build detailed profiles of your individual behavior in order to better sell you useless crap. Every single major internet ad company now uses behavioral tracking. Also, to comply with national copyright, many companies only make their services available to some internet users, those who reside in the ‘right’ country.
There are many ways that Bitmask and VPN’s in general can help:
Protect against ISP surveillance: A VPN eliminates the ability of your ISP to monitor your communication. They have no meaningful records which can be used against you, either by marketers or the government.
Bypass government censorship: An VPN can entirely bypass all government censorship, so long as you still have access to the internet. Note, however, that careful analysis of your traffic could reveal that you are using an VPN, which may or may not be legal in your jurisdiction. In particular, no VPN can hide your traffic from the NSA or GCHQ.
Access the entire internet, regardless of where you live: A VPN allows you to pretend to be in any country where we have a VPN gateway server. This gives you access to restricted content only available in those countries. A VPN also allows you to use services that may be blocked in your country.
Secure your Wi-Fi connection: Any time you use a public Wi-Fi connection, everyone else using that access point can spy on your traffic. A VPN will prevent this.
Keep websites from logging your IP address: Most all websites will log your IP address and some even retain this information for several years. Because your IP address is effectively an unique identifier that is connected to your real identity and your real location, there are many reasons why someone might not want every website they visit to have access to this personal information.
There are thousands of VPN offerings. Most free ones are scams that collect your information to sell to data brokers. Many more are closed sourced, unaudited, implemented in ways that leaks your information, and overstate what they can do.
Bitmask is different. It is an open source VPN built by the LEAP Encryption Access Project. It is one app that allows you to connect to multiple trusted VPN providers who use the LEAP VPN stack. Bitmask is third party audited by both Cure53 and Security Research Labs, fast, secure, super easy to use and free! You just install it and run it — zero configuration, zero registration. Bitmask and our partner providers do not require a user account, keep logs, or track you in any way.
As with all VPNs, users move their trust from their ISPs to the operators of the VPN. That’s why its super important to know who your VPN provider is. Bitmask only partners with VPN providers that have a long history of protecting and fighting for their users privacy.
Bitmask is open source: The Bitmask application and the platform it communicates with are both 100% open source which allows anyone to use and investigate the system, allowing for verifiable security and system integrity claims.
Does not leak traffic: Bitmask VPN is much better than other VPNs at preventing any unencrypted traffic from leaking from your computer (for example, because of IPv6, DNS, “Fail Open” leaks). These guarantees are on the Desktop version, but weaker on the Android version (because of limitations in what the Android OS will let us do).
No logging: Bitmask partner providers servers are configured by default to not keep any logs either for the VPN or domain name resolution. There is no logging beyond short term anonymized operational logs that help to monitor the health of the system.(Note - a nefarious private provider could manually modify this behavior.)
Semi-anonymous: Bitmask compatible providers enable VPN usage via an anonymous certificate as the verification method. So, there are no identities tied to single users, no accounts, no direct payments.
Firewall: extra firewalling to prevent data leakage (currently Linux and MacOS, Windows coming soon).
Kill switch: Provided in Linux, MacOS and Android with Windows coming soon.
Up to date: The Bitmask application is always kept up to date with the latest security patches for Android and Linux. Windows and Mac users currently need to update manually, but we’re working on automatic update mechanisms there as well.
Application integrity: When you download Bitmask from dl.bitmask.net, your service provider will not be able to distribute to you a compromised client with a backdoor.
More and more nation states control their populations by limiting their access to information on the open internet. Bitmask provides a variety of circumvention techniques that can allow users to bypass censorship. Bitmask and some of our partner providers offer Snowflake, Obfs4, Obfs4 + Kcp, Quic, our own Hopping Protocol, and are working on integrating obfuscated Wireguard and Masque in the near future.
Let’s first distinguish between four different types of security Human, Device, Message, and Network security. Human Security: Human behavior that keeps you safe and out of harms way. Device Security: The integrity of your computing devices to be free from hardware or software modifications that steal your information. Message Security: The confidentiality of messages you send and receive, and the pattern of your associations. Network Security: Protection of your internet traffic against behavioral tracking, account hijacking, censorship, eavesdropping, and advertising.
Bitmask only applies to Network Security. For example, it cannot improve your behavior, protect your device against viruses, or ensure your messages are end-to-end encrypted.
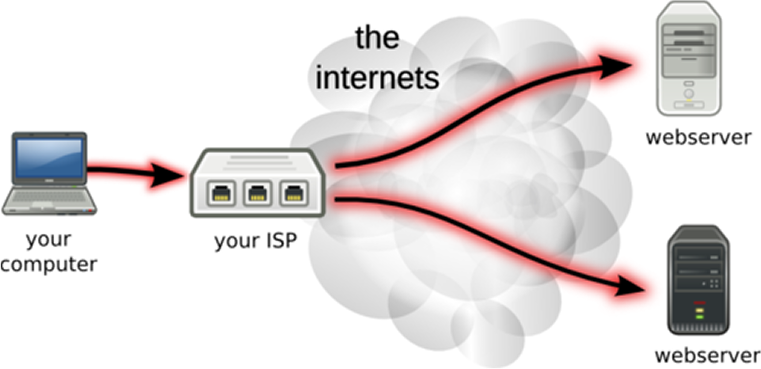 In a normal internet connection, all your traffic is routed from your computer through your ISP (Internet Service Provider) and out onto the internet and finally to its destination. At every step of the way, your data is being recorded and is vulnerable to eavesdropping or man-in-the-middle attacks.
In a normal internet connection, all your traffic is routed from your computer through your ISP (Internet Service Provider) and out onto the internet and finally to its destination. At every step of the way, your data is being recorded and is vulnerable to eavesdropping or man-in-the-middle attacks.
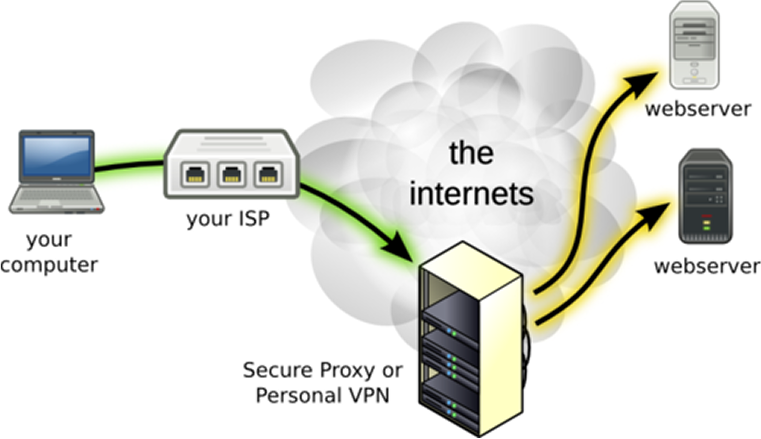
With an VPN, your traffic is encrypted on your computer, passes through your ISP and on to your VPN provider. Because the data is encrypted, your ISP has no knowledge of what is in your data that they relay on to your VPN provider. Once your data reaches the VPN provider, it is decrypted and forwarded on to its final destination.
With Bitmask, if your data is not using a secure connections then it is still vulnerable from the point it leaves the VPN Gateway. However, by routing your data through the VPN provider, you have achieved two important advantages:
Your data is protected from blocking, tracking, or man-in-the-middle attacks conducted by your ISP or network operators in your local country.
Your data now appears to use the IP address of the VPN provider, and not your real IP address. Most websites gather and retain extensive data base on this IP address, which has now been anonymized.
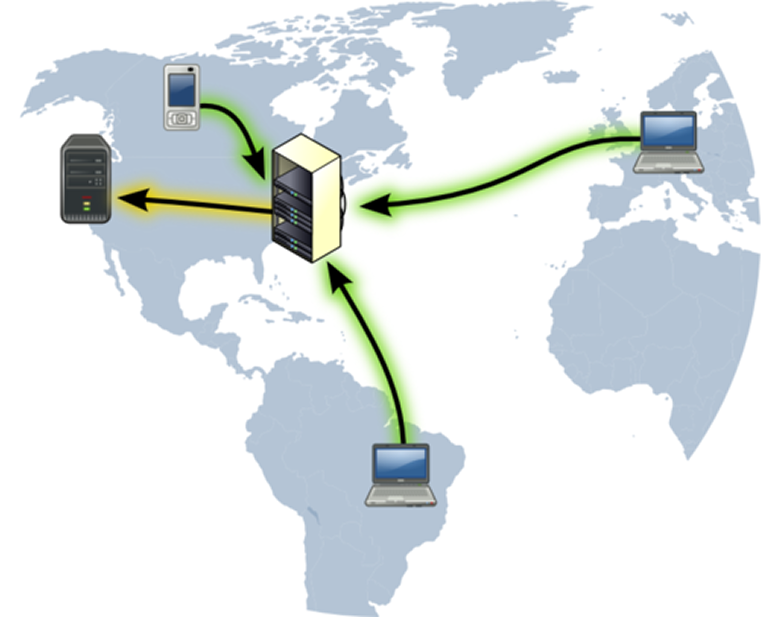
Because your traffic appears to originate from the VPN provider, the recipient of your network communication does not know where you actually are (unless, of course, you tell them). Additionaly, your traffic has been mixed together with the traffic of hundreds or even thousands of other people.
In the case illustrated above, the Web Servers thinks that the laptop in Europe, the laptop in Africa, and the cellphone in Asia are all coming from New York, because that is where the VPN gateway is.
Powerful attackers: Very large spy agencies from the US and UK, like the NSA and GCHQ, have the ability to monitor all traffic everywhere on the internet. With this capability, we know that they will identify VPN traffic and correlate where this traffic originated. Because of this, using a VPN might actually invite more scrutiny from the NSA or GCHQ than not using anything at all. Generally, VPNs are not providing anonymity against a global adversary. People who require strong anonymity tools that protect against targeted attacks should only rely on specialized software such as Tails running on Tor.
Legality: If you live in an non-democratic state, it may be illegal to use a VPN or personal VPN to access the internet that has not been approved by the government.
Mobile network: Using a VPN on your mobile device will secure your data connection, but the telephone company will still know your location by recording which towers your device communicates with.
An insecure connection is still insecure: Although Bitmask will anonymize your location and protect you from surveillance from your ISP, once your data is securely routed through your provider it will go out on the internet as it normally would. This means you should still use SSL or TLS when available.
VPN only applies to network security: Using a VPN will not protect your communication if your computer is already compromised with software or hardware that is stealing your personal information. Also, if you give personal information to a website, there is little that a VPN can do to maintain your anonymity with that website or its partners.
Browser fingerprints: Every web browser effectively has a fingerprint that can uniquely identify your web traffic from everyone else. Although websites rely on cookies for tracking, a powerful network observer could use the uniqueness of your browser in order to de-anonymize your traffic.
The internet might get slower: the Bitmask VPN routes all your traffic through an encrypted connection to your provider of choice before it goes out onto the normal internet. This extra step can slow things down. To minimize the slowdown, try to choose a VPN gateway server close to where you actually live.
Anonymous proxies: There are some websites that block access from “Anonymous Proxies”. For this reason, depending on which VPN gateway you are using, your traffic might be blocked.